As you may know, I also had my own custom kernel for the Xiaomi Mi 9 SE.
It of course, uses the given trees from Xiaomi.
But as the time keep changing, they still don't give a frick about updating their codes even the built-in kernel on their latest ROM is already had so many improvements and changes over the sources that they uploads on their GitHub.
Firmware
So, the device firmware is another things that we need for partial or full functionality of certain hardware devices.
And as you can see on your kernel tree, these binary blobs are usually proprietary because some hardware manufacturers do not release source code necessary to build the firmware itself.
But thankfully, since it was just a binary blobs, it is relatively easy to dump it from the pre-compiled kernel.
Prepare
Before starting, we should have atleast :
- decompressed kernel binary (use
unpackbootimgto get theImage.gzand extract theImagefile fromImage.gz) - the old firmware binary for the magic number references (you can get it on the output directory of your kernel or converting the ihex files)
csplitbfor binary splitting (https://github.com/mypalmike/csplitb)xxdfor inspecting the binaries.ddfor dumping an actual firmware.avr-objcopyfor binary blobs to ihex conversion.
Finding the magic number
The magic number is needed for csplitb to identify the content header.
So, we need to get it from the old firmware binary files.
$ xxd <Original-Firmware> | head -n1
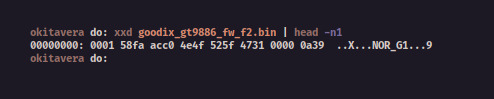
We just need the 8 number of it, which is 0001 58fa
Inspecting the kernel binary
Before splitting, better if we just check the kernel binary if it has that magic number.
$ xxd <Kernel-Image> | grep '0001 58fa'
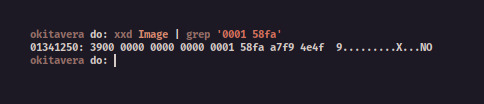
Yay, we found it!
Splitting firmware from kernel
Since we figured out that the kernel image is actually contains the firmware that we need, then let's just split it with csplitb.
$ csplitb --prefix dumped-fw- --suffix .bin --number 4 000158fa <Kernel-Image>
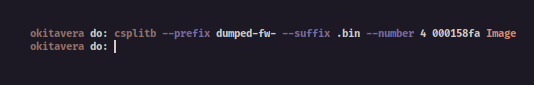
And the result will be saved on dumped-fw-0000.bin.
Get the right content of the firmware
To get the right right content of the actual firmware, we need to find out the exact size of the original firmware.
$ stat -c %s <Original-Firmware>
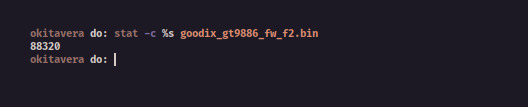
And lets dump it with dd.
$ dd if=dumped-fw-0000.bin of=<New-Firmware-Name.bin> bs=<Size-Of-Original-Firmware> count=1
Convert the new firmware to Intel Hex files
Since we want to include it in our kernel trees, we should convert it from a binary blobs to Intel Hex.
We can do that using avr-objcopy.
$ avr-objcopy -I binary -O ihex <New-Firmware.bin> <New-Firmware.ihex>
And tadaaaa.. the new firmware is ready to cooks into the kernel.
androidlinuxkernel

